INSUBCONTINENT EXCLUSIVE:
Thousands of ransomware victims may finally get some long-awaited relief.
New Zealand-based security company Emsisoft has built a set of
decryption tools for Stop, a family of ransomware that includes Djvu and Puma, which they say could help victims recover some of their
files.
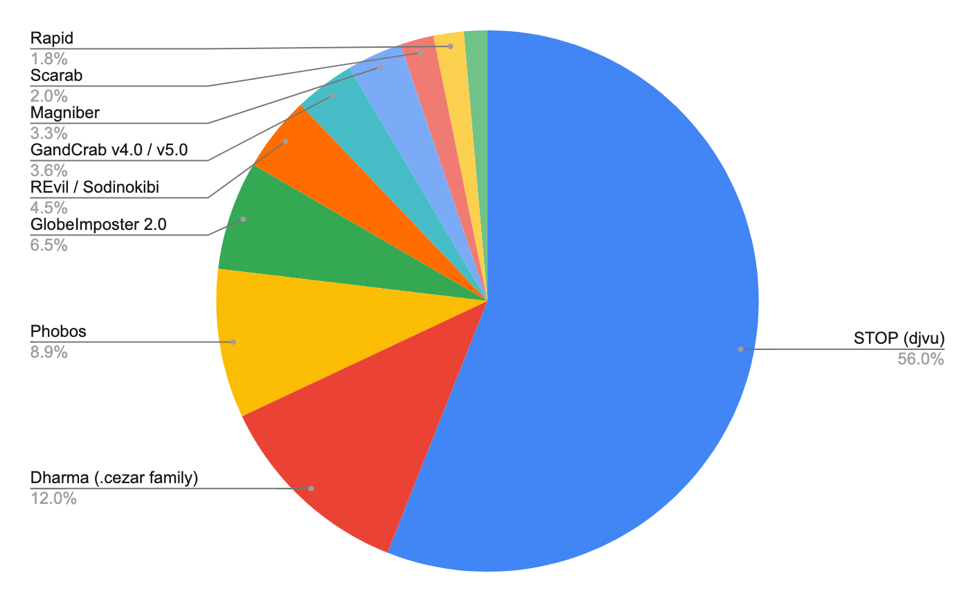
Stop is believed to be the most active ransomware in the world, accounting for more than half of all ransomware infections, according
to figures from ID-Ransomware, a free site that helps identify infections
But Emsisoft saidthat figure is likely to be far higher.
If you&ve never had ransomware, you&re one of the lucky ones
Ransomware is one of the more common ways nowadays for some criminals to make money by infecting computers with malware that locks files
Once the Stop ransomware infects, it renames a user files with one of any number of extensions, replacing .jpg and .png files with .radman,
.djvu and .puma, for example
Victims can unlock their files in exchange for a ransom demand — usually a few hundred dollars in cryptocurrency.
Not all ransomware is
Some security experts have been able to unlock some victims& files without paying up by finding vulnerabilities in the code that powers the
ransomware, allowing them in some cases to reverse the encryption and return a victim files back to normal.
Stop is the latest ransomware
that researchers at Emsisoft have been able to crack.
The latest known victim count is about 116,000
It estimated that about one-quarter of the total number of victims.Emsisoft
It more of a complicated decryption tool than you would
normally get,& said Michael Gillespie, the tools& developer and a researcher at Emsisoft
&It is a very complicated ransomware,& he said.
In Stop case, it encrypts user files with either an online key that pulled from the attacker
server, or an offline key, which encrypts users& files when it can''t communicate with the server
Gillespie said many victims have been infected with offline keys because the attackers& web infrastructure was often down or inaccessible to
the infected computer.
Here are how the tools work.
The ransomware attackers give each victim a &master key,& said Gillespie
That master key is combined with the first five bytes of each file that the ransomware encrypts
Some filetypes, like .png image files, share the same five bytes in every .png file
By comparing an original file with an encrypted file and applying some mathematical computations, he can decrypt not only that .png file but
other .png of the same filetype.
Some filetypes share the same initial five bytes
Most modern Microsoft Office documents, like .docx and .pptx, share the same five bytes as .zip files
With any before and after file, any one of these filetypes can decrypt the others.
There a catch
The decryption tool is ¬ a cure-all& for your infected computer, said Gillespie.
The victim has to find a good before and after of
basically every format that they want to recover,& he said.
Once the system is clean of the ransomware, he said victims should try to look
for any files that were backed up
That could be default Windows wallpapers, or it can mean going through your email and finding an original file that you sent and matching it
with the now-encrypted file.
When the user uploads a &before and after& pair of files to the submission portal, the server will do the math
and figure out if the pair of files are compatible and will spit back which extensions can be decrypted.
But there are pitfalls, said
Gillespie.
Any infections after the end of August 2019, unfortunately there not much we can do unless it was encrypted with the offline
If an online key was pulled from the attacker server, victims are out of luck
He added that files submitted to the portal have to be above 150 kilobytes in size or the decryption tools won''t work, because that how
much of the file the ransomware encrypts
And some file extensions will be difficult if not impossible to recover because each file extension handles the first five bytes of the file
differently.
The victim really needs to put in some effort,& he said.
The current share of worldwide ransomware infections (Image:
Emsisoft)
This isn''t Gillespie first rodeo
For a time, he was manually processing decryption keys for victims whose files had been encrypted with an offline key
He built a rudimentary decryption tool, the aptly named STOPDecrypter, which decrypted some victims& files
But keeping the tool up to date was a cat and mouse game he was playing with the ransomware attackers
Every time he found a workaround, the attackers would push out new encrypted file extensions in an effort to outwit him.
They were keeping
me on my toes constantly,& he said.
Since the launch of STOPDecrypter, Gillespie has received thousands of messages from people whose
systems have been encrypted by the Stop ransomware
By posting on the Bleeping Computer forums, he has been able to keep victims up to date with his findings and updates to his decryption
tool.
But as some victims became more desperate to get their files back, Gillespie has faced the brunt of their frustrations.
The site
moderators were patiently responding
They&ve kept the peace,& he said
&A couple of other volunteers on the forums have also been helping explain things to victims.
There been a lot of community support trying
to help in every little small bit,& he said.
Gillespie said the tool will also be fed into Europol No More Ransom Project so that future
victims will be notified that a decryption tool is available.
The sinkhole that saved the internet